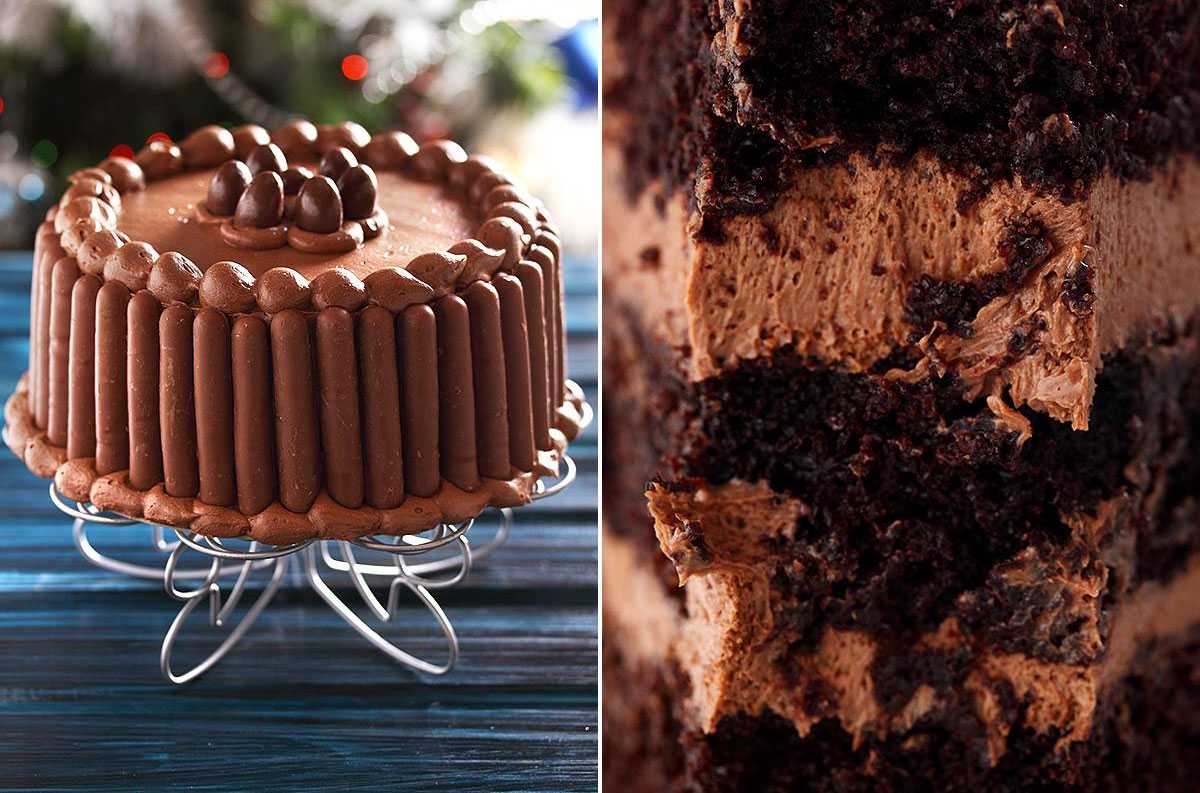Торт с орехами и карамелью приготовить легко! Простые продукты, подробный рецепт, а тарт получается
Норвежский торт - один из самых лучших в мире, попробуйте приготовить такое лакомство. Торт
Ищете Торт пьяная вишня пошаговый рецепт с фото ? Подробный рецепт с фотографиями и
Как приготовить домашние шоколадные торты с добавлением сгущенного молока и какао
Торт Красный бархат – простой рецепт вкуснейшего домашнего торта на кефире. Кулинарные советы, нужно
Сегодня мы представим вам новый рецепт традиционного торта «Наполеон» с вареной сгущенкой, в состав
Главный "секрет" торта Наполеон, приготовленного в домашних условиях \ Классический рецепт из советских времен
На связи ваш бессменный консультант по десертам Оля Афинская с последним постом этого года
Маково-ореховый торт со сметанным кремом Тесто: 140 г (1 ст.) муки 170 г (1
Как приготовить пошагово меренговый торт в домашних условиях. Что такое меренга и ее особенности.
Наполеон классический - 10 пошаговых рецептов в домашних условиях. Заходите на kylinariya.ru - будет
Если вы любите соленую карамель и шоколад, этот торт с соленой карамелью и шоколадным
Попробовав однажды этот домашний торт станет вашим любимым десертом! Наполеон Афганский получается очень большой
Искусно приготовленный торт с малиной станет прекрасным дополнением к чашке чая и украшением праздничного
Шоколадная глазурь из какао - отлично подходит для торта "Птичье молоко", глазировки пончиков, а
Многие просто обожают вкусный и нежный медовик, который в буквальном смысле тает во рту.
Как приготовить бананы в карамели в домашних условиях? ➤ 5 лучших проверенных рецептов: жаренные
Крем из творожного сыра для торта - 10 рецептов приготовления. Заходите на kylinariya.ru -
Оригинальный торт для любого праздника. Стоит немного потрудиться, ради такого прекрасного результата! Отдельного внимания
Торт медовик приготовить сможет абсолютно любой, это не сложно, да и конечный результат стоит
Шоколадный торт Спартак в домашних условиях. Разнообразные проверенные рецепты приготовления с подробным описанием процессов
Как приготовить вкусный шоколадный торт с орехами быстро и просто в домашних условиях; с
Торт Эстерхази - это тонкие ореховые коржи и масляный крем, типа Шарлот. Что-то наподобие
Приготовление действительно красивого и пышного бисквита – это настоящее искусство. Но мы уверены, что